How does OpenAM work with Windows Desktop SSO ?
Or Kerberos Desktop SSO with OpenAM and Active Directory.
Or OpenAM and Windows Desktop SSO .
Or Using the windows desktop Single sign on with Openam.
Or OpenAM Windows Desktop SSO Authentication
On your openam IDP instance login and go to
Access control > realm (root or whichever realm you are
using) >Authentication >
(Here I am showing you how to get windows desktop sso and in
case it doesn’t work for some reason it will fall back to web login where openam login screen will still allow you to
login with user id password) If you just want windows desktop sso this solution will still work just don’t
use “ldapService” module in authentication chain below.
1. You can create another module for Active Directory
service as shown below and let’s call it as “DataStore”. (Here we assume you
have already configured active directory)
2. Create new module instance of type windows
desktop sso
Now click on your windowsDesktopSSO module
instance and configure with your keytab files. (How to generate keytab files
is a separate topic. Here I am assuming you have some knowledge of it already)
Now still on the same page Access control > realm (root or whichever realm you are using) >Authentication
• Go to “Authentication Chaining” section.
• Create new authentication chaining called “WinDesktopSSOAuthChain”
• Add windowsDesktopSSO module as primary module and for fall back add “DataStore” module which will use Active directory in case desktop sso fails. (If you don’t want exclude Datastore module here)
Also we can create another authentication chain called
“ldapservice” which will use you Active Directory (ie. Use the Data store
module we created above)
So now when you are at Authentication tab you will see
• Two module instances (DataStore, windowsDesktopSSO)
• Two Authentication Chaining items(WinDesktopSSOAuthChain and ldapservice)
All we now need to tell openam is what “authentication chain” to use for aunthentication.
For
Organization Authentication Configuration:==> WinDesktopSSOAuthChain
Administrator Authentication Configuration:===> ldapService
By doing this we are telling openam to use “ldapservice” for Admin authentication and
“winDesktopSSOAuth” chain for user’s verification.
Some more links that may be helpful
Once the above settings are done we still need to tweak the browser settings so that browser can send kerberos token.
Configuring
the browser for SSO with OpenAM
or configuring Internet explorer for sso with OpenAm
or configuring Firefox for sso with OpenAm
or configuring Chrome for sso with OpenAm
Let’s assume the OpenAM idp url that you are using is http://idp.abc.com.
The OpenAM IDP returns a “401” authorization error to the
browser. Each browser responds differently to this 401. What we want is for the
browser to attempt authorization with the Kerberos data.
Internet Explorer
By default IE will automatically send your logged-on Windows
credentials only to Intranet web sites. The OpenAM IDP can be manually added to
the trusted list of Intranet sites until we can engage systems engineering to
set it up as a web site that can be automatically recognized as Intranet (and
therefore trusted).
1.
Check the User Authentication settings: Click Tools – Internet Options – Security –
Local Intranet. Click the “Custom Level” button, and scroll to the User
Authentication section.
1.
Add the IDP to the list of trusted intranet
sites. Click Tools – Options – Local Intranet. Click the “Sites” button, and then
click the “Advanced” button.
s
You may also do this via a manual registry update as shown
below:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\EscDomains\abc.com\idp]
"http"=dword:00000001
Confirm Windows Integrated Security. Click Tools
– Options – Advanced. Scroll down to the security section and ensure “Enable
Integrated Windows Authentication” is checked.
d You are done with IE settings.
Configuring Chrome for sso with OpenAm
Chrome uses the same internet settings as IE, so once
IE works, Chrome works too. To confirm this, click Settings, then type network
into the search box. Click the “Change Proxy Settings” button. You should see
the same Internet Explorer dialog.
Configuring FireFox for sso with OpenAm
When Firefox gets the 401, it can be configured to fall
back to a negotiated authentication protocol that achieves SSO. Firefox must be
configured to trust the OpenAM IDP for this negotiation to be successful. Launch
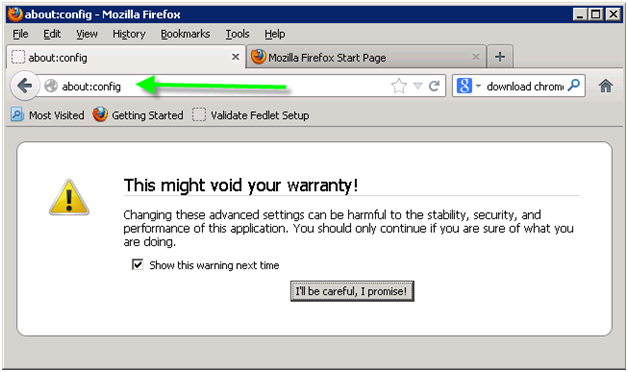
Firefox, and in the address bar, type about:config
Click the “I’ll be careful” button. In the Search box, type network.negotiate to filter the
configurations to only the network negotiation options. Change two values.
Both values will be the same. Use the appropriate IDP for the environment you
want to test in.
(1)
network.negotiate-auth.delegation-uris
(2)
network.negotiate-auth.trusted-uris
Note: If you have
more than one URL that you need to add you can add a COMA SEPARATED LIST in
firefox. (For this example I will consider another idp say idp.xyz.com)
In order to make Firefox send the Kerberos ticket you can
also use about:config to set
network.automatic-ntlm-auth.trusted-uris
With this configuration your windows desktop SSO setup should work.
If you liked this article or have suggestion or correction please post your valuable comments.